Get files of the Wildlifecamera WK 4 HDW
For the impatient people, just go directly to tl;dr section.
A friend of a friend bought the wildlife camera Maginon WK 4 HDW, there was a nice price at Aldi. The installation of the camera was very streamlined and there is a very good video quality.
They advertised the camera with an WiFi access to acquire the video.
And with that the problem started, to conserve battery power the cameras Wifi mode is activated via Bluetooth LE, which isn’t this bad… Just that with the original app you manually need to change the WLan in the smartphone. That’s specially not easy for computer illiterate persons.
So, they needed to ne found a different solution.
As resultat we have now an Raspberry Pi which regulary fetching the videos and easily can be played with just a doubleclick.
So, let us go step-by-step through the process.
Since we know that we need to activate the Wifi of the cam via BTLE we need to snoop on the bluetooth connection, also we need to capture the webtraffic for getting the API endpoints.
We need several gadgets and tools:
- A smartphone, I used an Moto 5G.
- PCAPdroid - Capturing the webtraffic
- Wireshark - Visualize the captured data
- WildlifeCamera - We need the stock app for creating the data which we need to analyze
First we need the API endpoints:
- Open PCAPdroid
- Start the recording
- Start the WidlifeCamera App and connect to the camera
- Go into Media, to be sure change also in the video tab
- Disconnect the camera
- Open the file in Wireshark

- With a bit of scrolling and reading we find this API endpoints, I am sure there are more, but right now we just want to download the files.
ping firmware/wifi settings battery storage files/busy files/details files/full/{id} files/delete [JSON POST] --> [id] reboot [POST] - For us just the files/ and reboot commands are useful, so we are done with getting the endpoints
Let us now go for the bluetooth sniffing:
- Enable ‘Bluetooth HCI snoop log’ in the developer options
- Toggle bluetooth off/on, or the snoop will not starting
- Start the WidlifeCamera App and connect to the camera
- Disconnect the camera
- Toggle bluetooth off
- Use adb for downloading the bugreport
adb bugreport bugreport - Open the zip file and locate the .cfa files in
'FS/data/misc/bluetooth/logs' - Open the cfa file in Wireshark
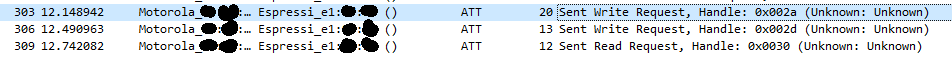
- We see that two write commands are issued, one to the handle 0x002a and one to the handle 0x002d. After that it reads from the handle 0x0030. The first write-command is the defined wlan access key as simple byte, the second one only a 1… The read from the handle seems just to return the success of the switching.
- Oh, let us check for Mac adress of the camera, we need that for the accessing it in the next step. (Or grab it from the wireshark output)
hcitool scan | grep Wild - So, let us use gatttool and let us send the commands
gatttool -b [bluetooth adress] -I
connect
char-write-cmd 0x002a 34373131
char-write-cmd 0x002d 01
char-read-hnd 0x0030
- You should hear a click in the camera, and few seconds later the wlan should be available.
Now we have the Wifi of the camera activated, we will connect to it for some further testing. The camera is very quick with switching the Wifi off, so be fast.
-
First we will try to get a list of files, that’s done available
curl http://192.168.4.1/files/details -
This results in an JSON like output
So, we have now an id, filename, timestamp and a size…[ { "id": 42, "type": 1, "name": "100STLTH/STC_0024.AVI", "timestamp": 1630756062, "size": 155099812 } , { "id": 21, "type": 1, "name": "100STLTH/STC_0003.AVI", "timestamp": 1630747682, "size": 143954516 } ] -
Let us download a file and store it. Be patient, the download isn’t the fastest.
curl http://192.168.4.1/files/full/42 -
We are done, the camera needs to rebooted for getting back in normal work, this needs to be a POST request:
curl -X POST http://192.168.4.1/reboot -
So, this is done now, we are able to activate the wifi of the cam, we are also able to download a video and putting the camera back to normal work.
I wrote a tiny Python script which actually is downloading the content of the camera. After I sanitize the output I will upload it to github and link it here.
bottom Link to heading
1x Android Smartphone
1x PCAPdroid
1x Wireshark
Activate Wifi mode
- hcitool scan | grep Wild
- gatttool -b [bluetooth adress] -I
connect
char-write-cmd 0x002a [wlan key as byte]
char-write-cmd 0x002d 01
char-read-hnd 0x0030
API Endpoints (192.168.4.1)
- ping
- firmware/wifi
- settings
- battery
- storage
- files/busy
- files/details
- files/full/{id}
- files/delete [JSON POST] –> [id]
- reboot [POST]